Comprehensive Review of LinkDaddy Cloud Services
Comprehensive Review of LinkDaddy Cloud Services
Blog Article
Protect Your Data With Top-Tier Cloud Storage Solutions
In an age where information safety and security is paramount, entrusting your useful details to top-tier cloud storage services is a strategic relocation for securing against potential threats. These services exceed plain storage, offering advanced file encryption methods, rigid gain access to controls, and adherence to sector standards. By checking out the nuances of data defense within cloud storage remedies, you can elevate your organization's strength to cyber threats and ensure the long life of your digital possessions.
Relevance of Data Security
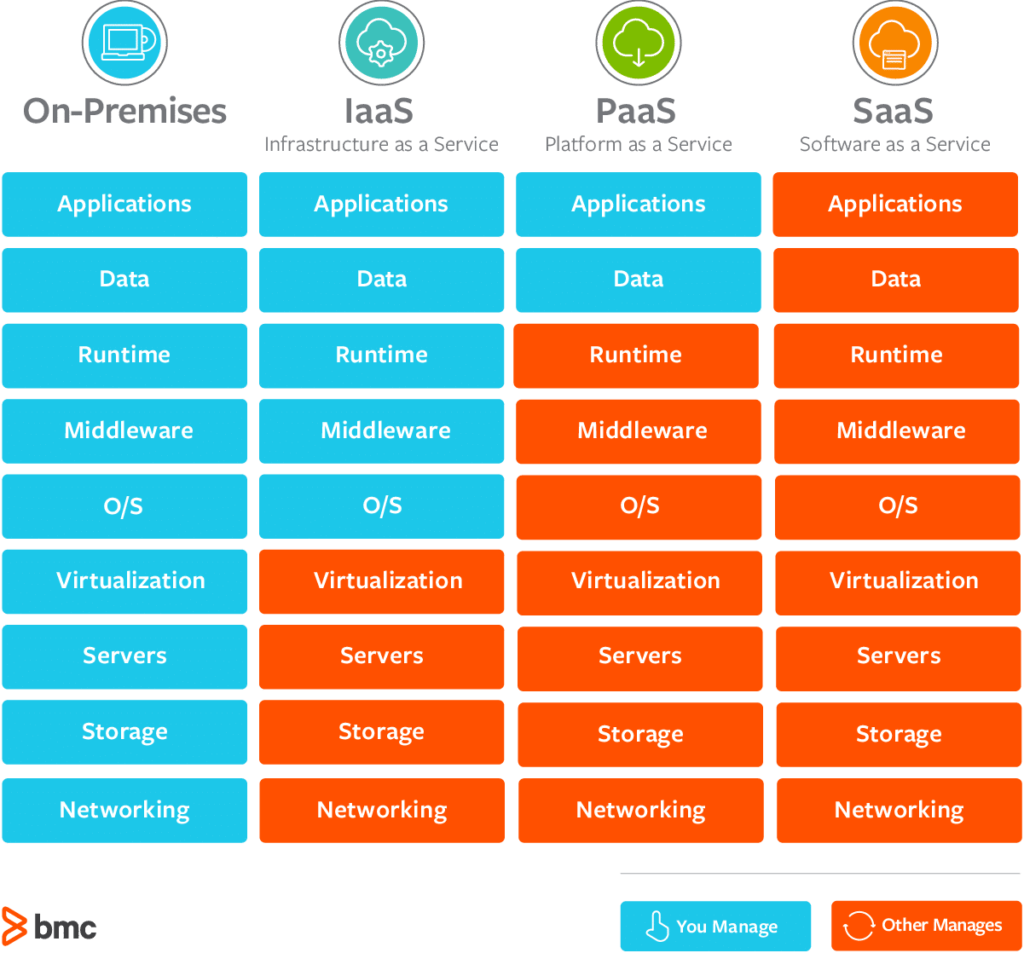
Applying robust information defense measures helps in keeping privacy, honesty, and schedule of data. File encryption, accessibility controls, and regular backups are vital components of a detailed data defense technique. Security transforms data right into a safe style that can just be accessed with the proper decryption secret, guaranteeing that even if data is obstructed, it stays unreadable to unapproved events. Access controls limit data accessibility to accredited individuals only, lowering the risk of internal violations. Regular backups create added layers of defense by making it possible for the repair of information in instance of accidental deletion, corruption, or cyber-attacks.
Advantages of Cloud Storage Space
In today's digital landscape, the utilization of cloud storage space supplies numerous advantages for companies and individuals looking for reliable and safe and secure information administration options. One crucial benefit of cloud storage space is its scalability. Users can quickly enhance or reduce their storage requires without the hassle of physical upgrades or hardware installments. This flexibility enables price financial savings and ensures that storage space capability aligns with present demands.
An additional significant advantage is the accessibility cloud storage supplies. Customers can access their data from any kind of place with a net link, promoting partnership and remote job capabilities. In addition, cloud storage uses enhanced data protection procedures such as encryption, redundancy, and regular back-ups. This lowers the risk of data loss because of hardware breakdowns, burglary, or natural catastrophes.
In addition, cloud storage space solutions frequently feature automated synchronization across gadgets, making certain that the most up-to-date version of files is offered in all times. In general, the advantages of cloud storage space make it a useful solution for contemporary information monitoring requires.
Key Features to Look For
When assessing top-tier cloud storage solutions, it is important to think about vital attributes that boost information monitoring effectiveness and safety and security. A robust cloud storage solution must use scalability options to suit your information development without jeopardizing performance.
Another vital feature is information encryption. Search for a cloud storage solution that offers end-to-end encryption to safeguard your data both en route and at rest. Security aids safeguard your delicate info from unauthorized access, guaranteeing data privacy and conformity with regulations.
Furthermore, seamless partnership devices are useful for teams working with shared projects. Seek cloud storage space solutions that use collaboration features like real-time editing, documents versioning, and individual authorizations control. These tools streamline operations processes and improve efficiency within your organization. Prioritizing these crucial features will certainly assist you choose a top-tier cloud storage space solution that satisfies your data administration needs successfully and safely.
Protection Procedures and Conformity
Guaranteeing robust safety actions and compliance criteria is extremely important for any kind of top-tier cloud storage solution supplier in safeguarding sensitive information (linkdaddy cloud services). To achieve this, leading cloud storage solutions implement a multi-layered technique to safety and security. This includes see it here encryption protocols to secure information both in transit and at remainder, robust accessibility controls to guarantee just authorized users can view or control data, and routine safety audits to determine and attend to any kind of susceptabilities proactively
Compliance with industry laws such as GDPR, HIPAA, or PCI DSS is also vital for cloud storage companies. Complying with these standards not only aids in safeguarding data yet also constructs trust with clients that rely upon these solutions to save their delicate info safely. Furthermore, top-tier suppliers frequently undertake third-party security accreditations to show their commitment to preserving high-security requirements.
Tips for Selecting the Right Service
To make an educated decision when choosing a cloud storage space solution, it is important to consider essential elements that line up with your organization's particular demands and concerns. Most importantly, evaluate the storage ability offered by the service copyright. Make sure that the storage space meets your present requirements and enables scalability as your information grows. Next, review the service's dependability and uptime guarantees to decrease potential downtime and ensure continuous accessibility to your information. Take into consideration the degree of safety and security measures applied by the copyright, such as file encryption protocols and information defense systems, to safeguard your sensitive information. In addition, check out the solution's compatibility with your existing applications and systems to simplify integration processes. Analyze the rates framework, consisting of any type of concealed prices, to establish the overall cost of the solution. Check out evaluations and seek referrals from trusted sources to evaluate the service supplier's track record anonymous and client satisfaction degrees prior to making a choice. By thoroughly thinking about these aspects, you can select a cloud storage service that finest fits your organization's demands.
Conclusion
Finally, guarding data with top-tier cloud storage space services is vital in ensuring the safety and security and stability of delicate information. By leveraging robust security measures, security protocols, and compliance criteria, companies can safeguard their data from cyber threats and information violations. Selecting a reputable cloud storage company that prioritizes information defense is vital for preserving discretion and availability while gaining from scalability and enhanced safety and security functions in the digital age.
With the boosting reliance on digital data storage, the danger of cyber hazards and data breaches has actually likewise grown.Applying durable data protection measures aids in maintaining privacy, stability, and availability of information. File encryption converts information into a safe and secure helpful hints format that can only be accessed with the appropriate decryption secret, making sure that also if data is obstructed, it remains unreadable to unauthorized events.Ensuring robust safety actions and conformity requirements is vital for any top-tier cloud storage solution provider in guarding sensitive information. By leveraging robust protection steps, file encryption procedures, and compliance criteria, organizations can safeguard their information from cyber dangers and data breaches.
Report this page